Can I trust the e-ID?
Or does China really know that I didn't brush my teeth yesterday if I vote "YES" to the e-ID on September 28th? We tested the technology behind the e-ID for you and would like to share our findings in this blog post.

To answer the China-question from the introduction directly: No, they don't, and if they do, it's certainly not because of the e-ID.
Last week, I found a "somewhat" questionable flyer in my mailbox depicting the Chinese flag alongside numerous surveillance cameras and other frightening images. As I read through the flyer, it quickly became clear to me that the publisher did (consciously or unconsciously) not understand the basic technology behind the e-ID or its use.

What is the e-ID?
The aim of the e-ID is to make personal identification completely digital. It can be used for various purposes. A simple example is the purchase of age-restricted goods or services such as alcohol or a cell phone subscription. Until now, this requires (more or less) tedious processes such as scanning or taking pictures of your ID for clear identification. The identification itself is then usually carried out by a person who has to check the information and approve the purchase.
The first problems with the current processes can already be identified here:
They usually take a long time and depend on manual steps.
There is a tendency to send too much information to the verifier, which is not used for the identification itself.
The verifier may be a dubious company that uses the data it receives for unwanted purposes.
What makes the e-ID better?
To avoid precisely these kinds of problems the e-ID is being developed with clearly defined goals and principles.
Only the information that is needed is transferred
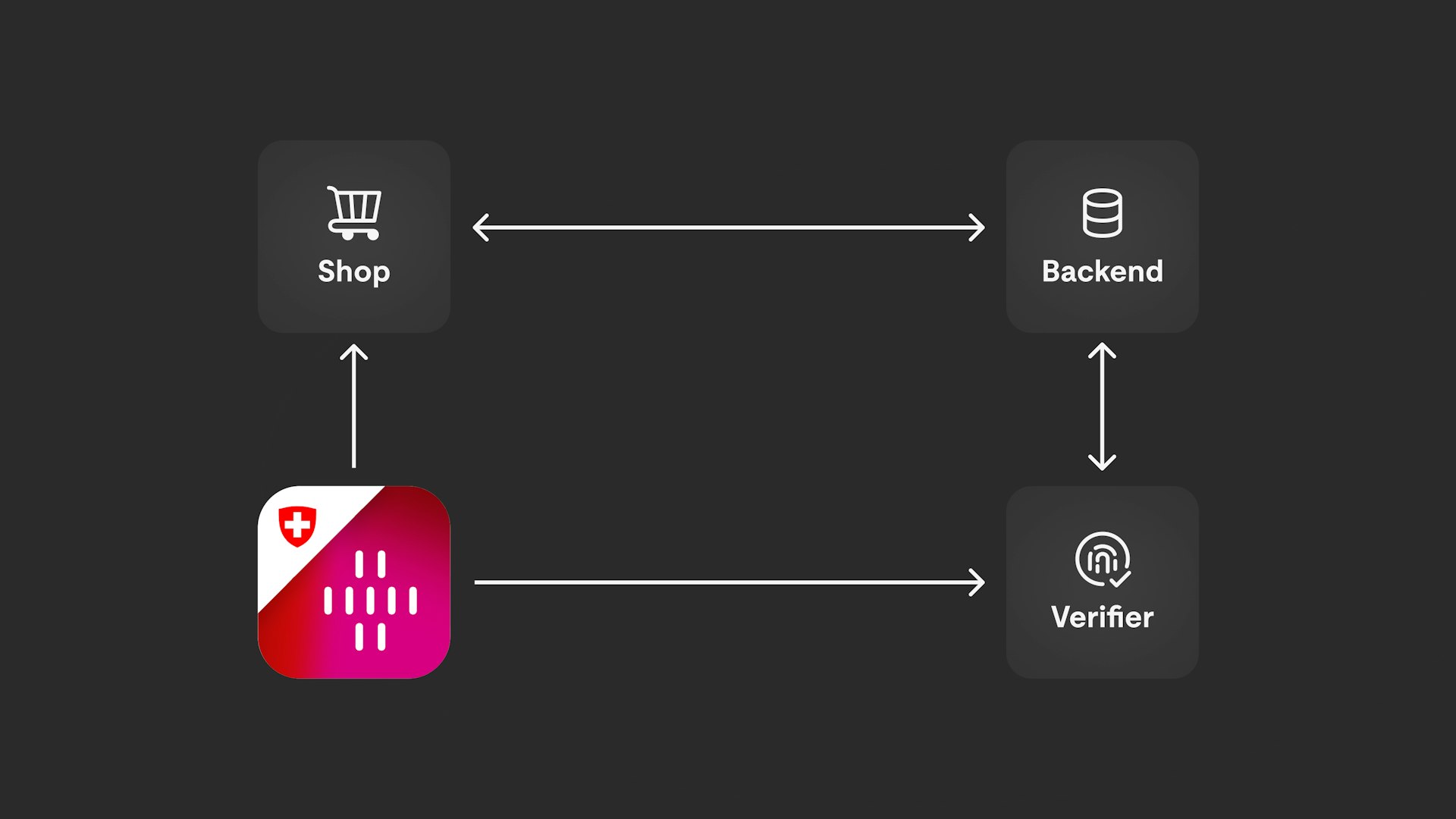
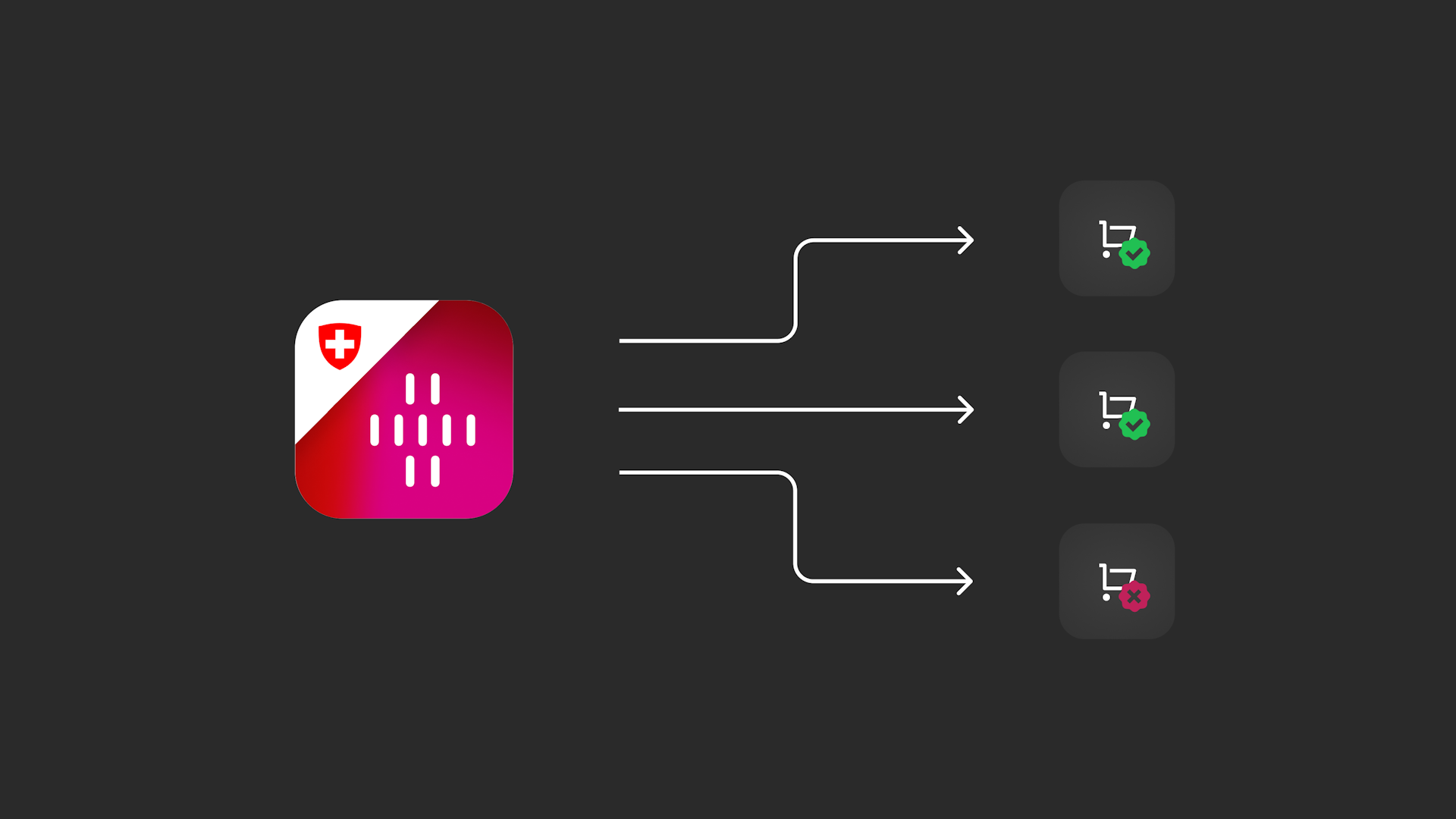
When verifying with an e-ID, only the personal information that is needed for the specific case is transferred. Before data is transferred, you receive a detailed overview of the information that is to be sent. You must consciously agree to this transfer.
This can be easily explained using the example of purchasing alcoholic beverages. To do this the seller only needs to know whether the person making the purchase is at least 16 or 18 years old. To verify this with the e-ID the seller only gets a "Yes" or a "No" as an answer if this is the case or not. The seller does not receive any further information such as the person's date of birth or full name.
Sellers must also be verified
A seller can only perform verifications using an e-ID if it has registered with the e-ID infrastructure and been verified there. With this step it also gets defined which information the provider is legally permitted to request and which it is not.
If the provider nevertheless requests too much data, the user is explicitly notified of this and can reject the request.
Local, decentralized data
All personal information is stored locally on the respective device. This means that sensitive data is not stored in the cloud, which minimizes the risk of it being stolen in the event of a hacker attack.
In addition the federal government acts solely as a verifying authority in data exchanges meaning that it does not know exactly what the data being exchanged will be used for in a transaction. This means that it is not possible to create so-called "citizen profiles".
Open Source
The federal government is developing the entire e-ID infrastructure as an open source solution on GitHub. This means that its code can be viewed by anyone at any time, which strengthens confidence in it.
Technology
The entire architecture of the e-ID infrastructure was developed and continuously improved in a participatory process involving the federal government and interested organizations and individuals. This has resulted in a very robust and modern foundation that meets the latest technical standards and the highest security requirements.
Conclusion
From a technical perspective the e-ID fulfills all the requirements for securely storing sensitive information such as identity documents or patient files and using it when needed. Data protection is also guaranteed by the approaches described above.
If you found these explanations about the e-ID too superficial, here you find our second Blogpost that goes into more detail about the technical aspects of the e-ID infrastructure: Die neue e-ID erklärt